The digital world is on the brink of a new revolution. With 5G networks rolling out globally and 6G already in research labs, the way we connect, communicate, and collaborate will be transformed forever. These wireless networks promise ultra-low latency, lightning-fast speeds, and the ability to connect billions—soon trillions—of devices. From autonomous vehicles and remote surgeries to industrial IoT and immersive extended reality, the future will be built on 5G and 6G infrastructure.
But alongside this promise lies an equally powerful risk: cybersecurity threats that could destabilize entire economies and societies. Unlike previous generations of wireless networks, 5G and 6G will not only handle voice and data—they will control critical national infrastructure, power mission-critical services, and form the digital backbone of future economies. A successful cyberattack on such a system could mean power outages, grounded airplanes, hacked medical devices, or even manipulated autonomous vehicles on highways.
The Expanding Threat Landscape in 5G and 6G
The reality is that 5G and 6G expand the attack surface exponentially. Every IoT sensor, smart car, medical device, or drone connected to the network becomes a potential gateway for hackers. The more connected the world becomes, the more vulnerable it is. And because 5G and 6G rely on cloud-native, software-defined architectures, attackers can exploit vulnerabilities not just in hardware, but in virtualized network functions, open interfaces, and third-party applications. In other words, the same innovations that make these networks powerful also make them attractive targets.
One of the most alarming aspects of 5G and 6G is how deeply they will intertwine with critical infrastructure. Energy grids, defense systems, air traffic control, and healthcare will all depend on them. If hackers compromise a 5G-powered hospital system, surgeries could be interrupted. If attackers infiltrate a 6G-enabled traffic network, autonomous vehicles could be manipulated. If a hostile nation-state launches a cyber campaign, it could cripple communications, disrupt economies, and threaten national security—all without firing a single bullet.
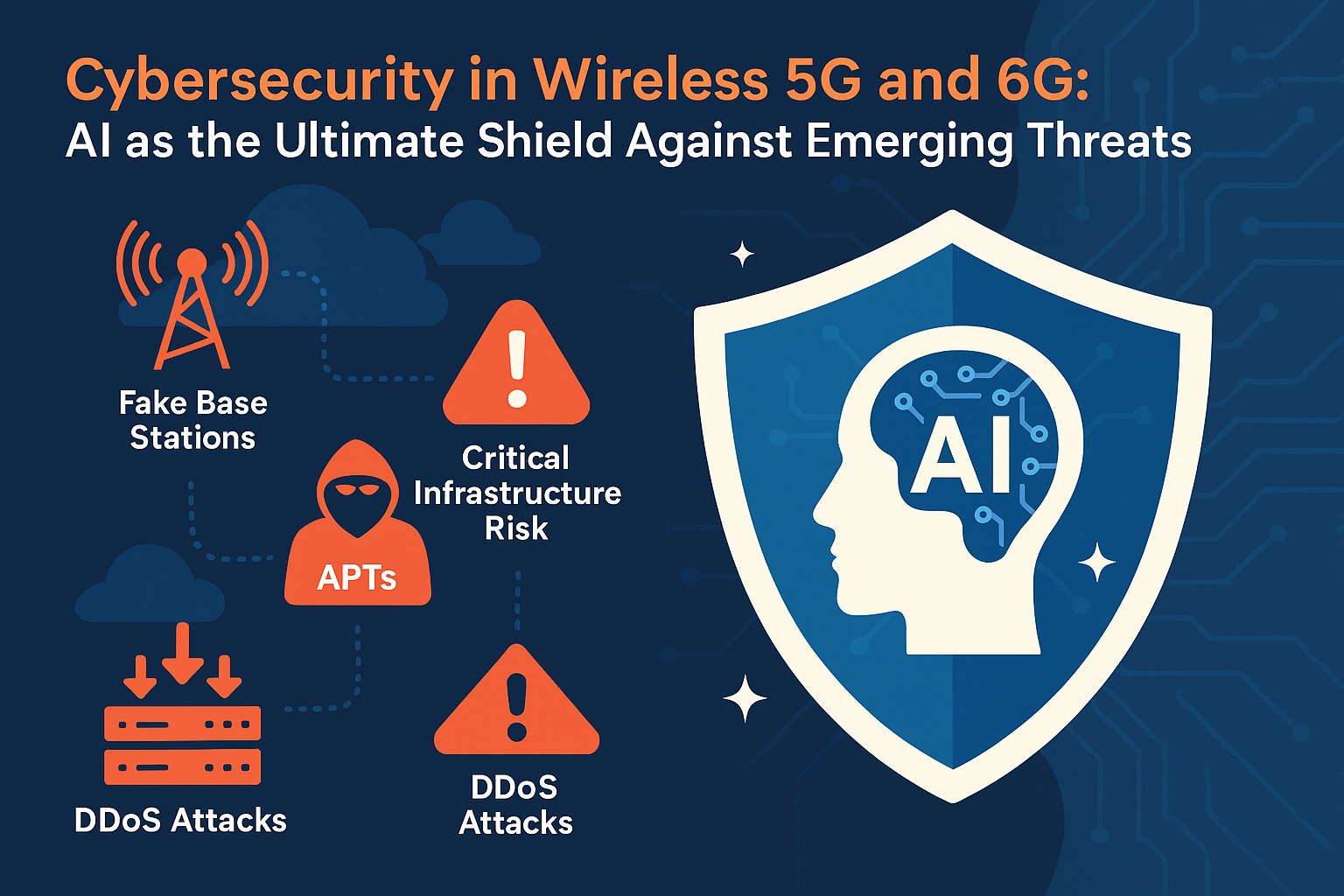
These threats are not theoretical. Already, researchers have demonstrated how fake base stations can track users, intercept calls, and steal identities. Distributed Denial of Service (DDoS) attacks fueled by hacked IoT devices have overwhelmed networks in the past—and with billions more devices joining 5G and 6G, the scale of such attacks will only increase. Meanwhile, advanced persistent threats (APTs) are targeting telecom operators, infiltrating their software supply chains, and implanting backdoors that can be activated later. And looming on the horizon is the quantum threat: once quantum computers become powerful enough, they could break today’s encryption standards, leaving 6G networks exposed unless they adopt post-quantum cryptography.
How Artificial Intelligence Becomes the Defense
So how can we fight back? The traditional methods of cybersecurity—firewalls, intrusion detection systems, manual monitoring—are no longer enough. The scale, speed, and complexity of attacks in 5G and 6G demand something smarter, faster, and more adaptive. This is where Artificial Intelligence (AI) steps in.
AI has the unique ability to learn from patterns, adapt in real time, and analyze massive amounts of data far faster than any human team could. In 5G and 6G networks, AI can act as a digital immune system, constantly scanning traffic, learning from anomalies, and stopping threats before they cause damage. Unlike static security systems, AI doesn’t rely only on known attack signatures; it can detect unknown and zero-day attacks by spotting deviations from normal behavior.
AI also enables predictive security. Instead of waiting for an attack to happen, AI models can analyze historical data, recognize attack patterns, and forecast potential threats. If attackers are probing a certain type of virtualized function across multiple networks, AI can identify the trend and help operators patch vulnerabilities before the exploit is launched at scale.
Another powerful advantage of AI is its role in securing the Internet of Things (IoT). Billions of IoT devices are notoriously weak when it comes to security, often running on outdated firmware with little to no authentication. AI algorithms can monitor device behavior, detect when a device is behaving abnormally, and quarantine it before it becomes part of a botnet.
For 6G, AI’s role will become even more critical. With 6G expected to integrate quantum communication, edge computing, and holographic data transmission, cybersecurity will need to operate in near real-time at the edge of the network. AI can power self-healing networks, where compromised nodes are automatically isolated, traffic is rerouted, and recovery happens without human intervention. It will also help deploy quantum-resistant encryption, making sure that even as quantum computers evolve, the integrity of 6G communications remains intact.
Building a Secure Future with AI and Trust
Real-world use cases already prove the value of AI in network defense. Telecom operators are deploying AI-powered intrusion detection systems to monitor their 5G cores. Smart cities are beginning to use AI for threat intelligence across public infrastructure, protecting traffic signals, surveillance systems, and energy grids. Hospitals leveraging 5G for remote surgeries are exploring AI safeguards that can detect and block latency injection attacks in real time. And in the automotive sector, AI is being trained to prevent signal spoofing attacks that could mislead autonomous vehicles.
The truth is clear: without AI, 5G and 6G cybersecurity would be overwhelmed by the scale of future threats. But with AI, these networks can not only survive but thrive—offering both innovation and security.
Organizations adopting 5G and preparing for 6G should start by building AI into their security frameworks from the ground up. That means implementing zero-trust models, upgrading encryption, using AI-powered monitoring tools, and investing in federated learning models where telecoms can share threat intelligence without compromising data privacy. Governments and enterprises must also prepare for the quantum era, ensuring their networks are resilient against the cryptographic challenges of tomorrow.
In the end, the success of 5G and 6G will not be measured only in speed, latency, or capacity. It will be measured in trust. People will only embrace smart cities, self-driving cars, and AI-powered healthcare if they trust that these systems are safe. Cybersecurity, therefore, is not just a technical issue—it is a matter of public confidence, national security, and global stability.
5G gave us speed. 6G will give us intelligence. But only AI can give us security. In the battle against cyber threats, AI is not just an option—it is the only shield strong enough to protect the networks of the future.